In
this
post we will show you the basic process of adding additional
clocks in Windows 10 and also a few neat Windows 10-only tricks to be
more productive while keeping up with different time zones.
How to Add Multiple Clocks in Windows 10 for Different Time Zones
Apart
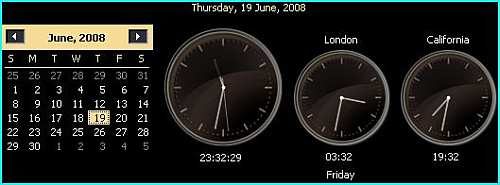
from your local clock, you can add up to two additional clocks to keep
up with different time zones. To do so, click on time and date in the
system tray on the far right corner. Time and a calendar will open with
the “Date and time settings” option below. Click on “Date and time
settings.”
In
date and time settings you will see options to customize your local
time clock. If you scroll down, you will see te “Add clocks for
different time zones” option. Click on it.
A
new dialog will open where you will see two clocks to be configured.
Check the checkbox next to the “Show this clock” option to enable and
configure that clock. You can select a time zone for that clock and also
name it to easily remember what time it will show. If you want to use
the other clock as well, check “Show this clock” and configure it
according to your needs.
When
you are done, you will see the time from both of these clocks by
hovering your mouse cursor over the time and date in the system tray.
You can also click on time and date to view these clocks.
Pin Multiple Time Zones to the Start Menu
Having
access to two clocks is great, but what if you could add as many clocks
as you would like? In Windows 10 you can pin any number of clocks to
the Start menu with time from different cities.
For this, click on
the Start menu and then click on “All apps.” Now click on the “Alarms
and Clock” app which should be at the start of the list under the “A”
section.
In
the Alarms and Clock app move to the “World Clock” tab, and you will
see a world map with your local time highlighted on it. Click on the “+”
sign at the bottom right corner, and you will be prompted to enter a
location.
Here
you can enter the name of the city/state you would like to see the time
for; if it is not mentioned in this list, try selecting a area closer
to your desired city/state. As soon as it is selected, the current time
in that area will be displayed on the world map. You can keep repeating
this process to add as many time zones as you would like.
Once
you are done adding time zones, you can easily pin them to the Start
menu. Just right-click on them and select “Pin to Start” from the menu.
The time will be added to the Start menu as a live tile, and you can
view it at any time from the Start menu. Keep repeating this process to
add all the required time zones to the Start menu.
Note: while viewing time in the Start menu, it may take a few seconds to update the current time and show it to you as a live tile.
Use Cortana to Instantly Check Time in Any Area
The
above methods are great for keeping up with the time zones that matter
to you, but what if you suddenly need to check the time in an area that
has not been pre-configured by you? Checking the World Clock or doing a
search in your browser might be the answer, but there is a faster
alternative as well.
You
can directly ask Cortana to show the current time in any area. All you
have to do is type “time in (your desired area),” and she will instantly
show you the time. For example, type “time in california,” and you will
see current time, date and day in California.
Conclusion
Keeping
up with time zones is really easy in Windows, and Windows 10 just made
things easier. The first method works fine in Windows 7 and 8 as well,
and it is still the quickest method to seeing the current time in a
different zone. Although, if you want to keep up with more than two time
zones, then the second method will surely help the Windows 10 users.